I want to see if this is a correlation with anyone else. My two victims (independent clients) had the Sexy/Porn.exe/x.mpeg hiding files via attribute change worm. I'm interested if others were in the same boat?

Posted 23 September 2013 - 11:50 AM
I want to see if this is a correlation with anyone else. My two victims (independent clients) had the Sexy/Porn.exe/x.mpeg hiding files via attribute change worm. I'm interested if others were in the same boat?
Posted 23 September 2013 - 11:52 AM
I want to see if this is a correlation with anyone else. My two victims (independent clients) had the Sexy/Porn.exe/x.mpeg hiding files via attribute change worm. I'm interested if others were in the same boat?
Yes, exact same payload.
Posted 23 September 2013 - 11:54 AM
I want to see if this is a correlation with anyone else. My two victims (independent clients) had the Sexy/Porn.exe/x.mpeg hiding files via attribute change worm. I'm interested if others were in the same boat?
Same here, but it was on a shared folder the user does not access.
Posted 23 September 2013 - 03:30 PM
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run "CryptoLocker" HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\RunOnce "*CryptoLocker"Please note that the * in front of the RunOnce value causes CryptoLocker to start in Safe Mode.
HKCU\Software\Microsoft\<random>Under these keys you will see Value names and their data with what appears at first to be garbage data (encrypted info). The droppers will also be found in the %Temp% folder and the main executable will be stored in a random folder under %AppData%. Last but not least, a startup will be created under HKCU\Software\Microsoft\Windows\Currentversion\Run to launch it.
Edited by Grinler, 15 October 2013 - 12:41 PM.
Updated with new info
Posted 23 September 2013 - 03:32 PM
Posted 24 September 2013 - 03:04 PM
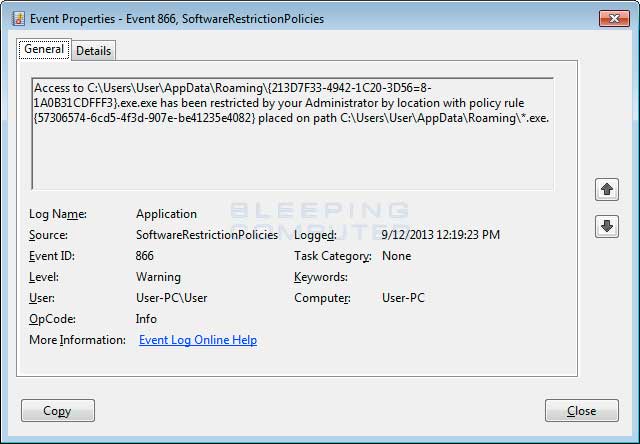
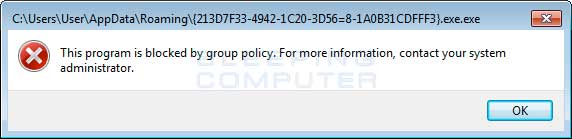
Craziness.. we deployed the SRP rules today blocking:
%AppData%\*.exe
%AppData%\*\*.exe
My concern is, has anyone run into issues with legitimate applications needing to run within AppData?
Posted 24 September 2013 - 03:18 PM
My concern is, has anyone run into issues with legitimate applications needing to run within AppData?
While there might be some applications that maybe could use it, off hand I can't think of anything. Any self-respecting software developer using settings/data in the user profile usually ensures a designated subfolder is created.
"Now faith is the substance of things hoped for, the evidence of things not seen."
Follow BleepingComputer on: Facebook | Twitter
Malware analyst @ Emsisoft | Follow me on Twitter
Posted 24 September 2013 - 03:38 PM
My concern is, has anyone run into issues with legitimate applications needing to run within AppData?
While there might be some applications that maybe could use it, off hand I can't think of anything. Any self-respecting software developer using settings/data in the user profile usually ensures a designated subfolder is created.
yeah that was my thought.. not worth the risk. ![]()
Posted 24 September 2013 - 08:00 PM
Serious Question:
So for those of you who actually paid the $100/$300 for the decryption key, do you actually have the key? Will that key work for everyone whose infected by this? I would assume it is the same encryption because there's 1 virus files going around.
Rants:
Who invented this type of encryption in the first place? The should be able to break it. NSA or FBI should be able to as I'm sure they have tools unknown to anyone outside that can do it easily with a click.
I've tried re-installing the ransomware, it does not re-infect and at this point I wouldn't even bother paying it cause I see some users have paid it and the encryption does not even work. I refuse to sit around for a trillion years and believe my excel/dbf files are forever locked up. Those are needed for work and I'm getting sick and tired of waiting for someone to break this thing.
Posted 24 September 2013 - 10:53 PM
Does anyone have the code for this? i did a clean up today and permanently deleted all of the executable before realizing what it was - i did note that the code can be captured using wireshark in the inital infecection. so anyone using packet capturing software you will be able to initiate the decryption yourself with the private key. what i dont understand is that the key is handed off during the infection - but i can not find where it embeds in the program
Posted 25 September 2013 - 02:43 AM
The key is saved on a remote server, This key is required to get all keys used to encrypt individual files. In other words, each key is different and there is no way you can break this.
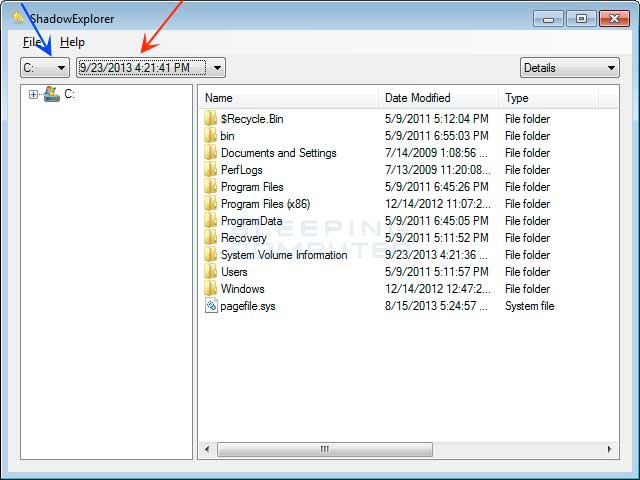
As stated also elsewhere in this topic your only choices are using ShadowExplorer or similar to try to retrieve a copy of the file before it was encrypted or using a backup.
"Now faith is the substance of things hoped for, the evidence of things not seen."
Follow BleepingComputer on: Facebook | Twitter
Malware analyst @ Emsisoft | Follow me on Twitter
Posted 25 September 2013 - 08:12 AM
Who Writes Malicious Programs and Why? Hackers and malware writers come from differnet age groups, backgrounds, countries, education and skill levels...with varying motivations and intents. Below are a few articles which attempt to explain who these individuals are and why they do what they do.Who invented this type of encryption in the first place?
.
.
Microsoft MVP Alumni 2023, Windows Insider MVP 2017-2020, MVP Reconnect 2016-2023
Microsoft MVP Consumer Security 2007-2015 
Member of UNITE, Unified Network of Instructors and Trusted Eliminators
Retired Police Officer, Federal Agent and Coast Guard Chief
If I have been helpful & you'd like to consider a donation, click 
Posted 25 September 2013 - 08:52 AM
The key is saved on a remote server, This key is required to get all keys used to encrypt individual files. In other words, each key is different and there is no way you can break this.
As stated also elsewhere in this topic your only choices are using ShadowExplorer or similar to try to retrieve a copy of the file before it was encrypted or using a backup.
My syntax was sloppy. I need the executable - The private key actually does get transferred at the time of infection and can be captured using wireshark - but of course how many of our customers are running packet sniffing utilities. My questions is if it is captured and seen with wireshark - where is it embedded on the infected machine?
Posted 25 September 2013 - 09:59 AM
Who Writes Malicious Programs and Why? Hackers and malware writers come from differnet age groups, backgrounds, countries, education and skill levels...with varying motivations and intents. Below are a few articles which attempt to explain who these individuals are and why they do what they do.Who invented this type of encryption in the first place?
- Who creates malware and why?
- Who Writes Malicious Programs and Why
- What goes through the minds of hackers?
- What is malevolent software intended for?
- What Makes Johnny (and Janey) Write Viruses?
- Malware Encryption Efforts...the bad guys are increasingly using better encryption
I think he was asking about encryption itself rather than malicious use of encryption. Basic overly simplified explanation of encryption and why it is used. Think of the purpose of encryption as like a safe with a programmable combination. Yes the encryption is of key importance for secure transfer of information. The way everything transfers across the internet, imagine that as a like sending it through snail mail... only in a world in which every postman on earth has the magical power to duplicate anything he touches leaving no way to know if the original has been touched.
Encryption is designed like a safe more or less. anyone can use encryption, and it is very difficult to open without the key. Different types require different levels of expertise. But due to the rapid spreading nature of expertise. (IE once one person knows how, he could write a tool and everyone on earth would know it, rendering the entire system nul). All in all, since the bad guys have access to more or less the same technology as the good guys, the world had to err on designing encryption strong enough that no known person can break it, the only other option was to automatically assume all information on any online transfer, has been spied upon.
Could it have been designed with say a "master key" that would allow the author of encryption to break it, not really. Ignoring that would create a single point of failure, an encryption standard with that weakness would never be adopted. Could you safely grant someone the power to see every bit of information that travels on the internet, as well as the ability to share that power with anyone, and safely say "oh yeah he would never misuse that".
Now is it possible the NSA or some group has actually figured out a weakness in this encryption? Absolutely possible, but it wouldn't be in their interest to admit they do. The assumption that no one has it, is what allows online sales to exist. If that assumption collapsed, the damage would be far worse than a few million people losing their data on the economic side, which isn't their concern at all anyway... the NSA is a spy organization. Just like it isn't their job to say, forward someone's phone records to help exonerate him in a murder trial, they wouldn't give up their edge over other countries just to help virus victims.
Posted 25 September 2013 - 11:03 AM
Hello everyone,
Is there any way to setup the Software Restrictions mentioned by Grinler on XP machines that DON'T have the Group Policy editor? I'm guessing through the registry, but would be unsure how to implement.
0 members, 0 guests, 0 anonymous users